Cyber security frameworks are structured guidelines that help companies manage and organize their information security practices. They come in different forms, including regulations, standards, directives, and best practices.
Frameworks can be mandatory, such as GDPR or NIS2, which have legal consequences if not followed, or voluntary, such as ISO 27001 and SOC 2, which set industry-wide expectations for information security. There are also frameworks for quality management (ISO 9001) or even specialized purposes like facility management (ISO 41001).
Frameworks clearly define what organizations need to achieve to be compliant or meet best practices, usually by setting a series of specific requirements or controls. However, frameworks typically don’t dictate how you achieve these goals.
For instance, a framework might require your company to implement two-factor authentication (2FA), but you decide which specific 2FA solution fits your processes best.
To help understand the topic clearly, here are a few definitions:
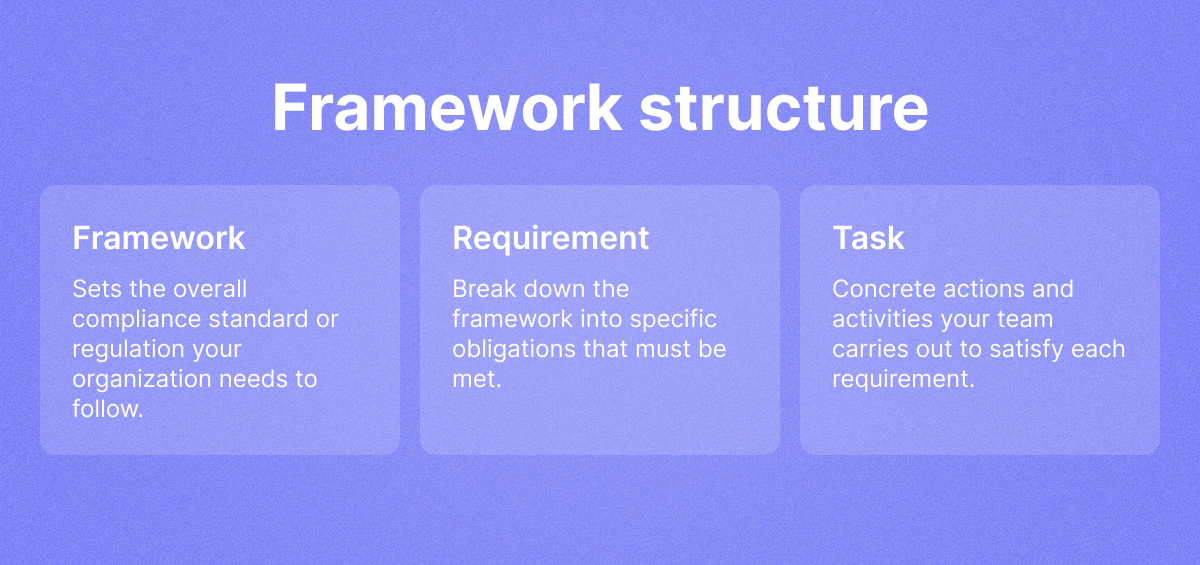
Framework: A structured set of guidelines or requirements, usually grouped into themes or categories, that outline objectives organizations must meet.
Standard: An agreed-upon set of best practices developed by international or national standards organizations (like ISO), usually voluntary but influential in establishing industry norms.
Directive / Regulation: Legally binding rules set by governing bodies (such as the EU) requiring compliance. Non-compliance may result in penalties.
Requirement: An objective or condition set within a framework or standard that an organization must meet.
Control: Specific actions or safeguards implemented by organizations to satisfy a requirement or reduce identified risks.
Why frameworks matter?
Cyber security frameworks typically originate from legal requirements or industry standards. Naturally, frameworks offer a set of best practices that cover the main risks or concerns associated to the frameworks theme and scope.
Legally required
Many requirements are set in the law. Regulations mandate that specific precautions are in place to protect organisations and nations from unnecessary cyber. and information risks.
Legal requirements are a common basis for frameworks, and they’re usually mandatory. Regulators, such as the European Union, national authorities, or specific industry bodies, set clear rules businesses must follow.
Examples of frameworks based on legal requirements include GDPR and NIS2 in the EU, HIPAA in the US and APPI in Japan.
Non-compliance can result in fines, reputational damage, and legal consequences. Enforcement of these frameworks is becoming stricter, especially in the EU and the US, as governments respond more proactively to cybersecurity threats.
Read more: What is GDPR?
Industry standards
Industry standards emerge from standards organizations like ISO and NIST, or directly from market demands, for example, SOC 2 certification for SaaS providers, or ISO 27001 for any organisation.
These standards help organizations demonstrate trustworthiness and adherence to best practices. Frameworks like ISO 27001 or SOC 2 align teams with both legal obligations and industry expectations, clearly signaling good security and privacy practices to customers, partners, and regulators.
Industry frameworks also significantly influence vendor trust. Companies prefer suppliers who can transparently demonstrate compliance with established standards. Meeting recognized frameworks can therefore provide a competitive advantage, and in some industries, certification has become essential.
Read more: What is ISO 27001?
Certifications and audits
Many frameworks, such as ISO 27001, allow organizations to receive official certifications through accredited audits.
During the audit process, an independent auditor reviews your compliance, verifies the implementation of required controls, and grants certification if all criteria are met. Certification offers external proof of your security practices, facilitating smoother interactions with customers and partners who rely on these assurances.
Read more: ISO 27001 Certification: What happens in the audit?
How frameworks are structured?
Cyber security frameworks generally follow a structured format, making it easier for organizations to understand and implement the necessary security measures. While the exact terminology and details differ, most frameworks include these core elements:
Chapters (themes or domains)
Chapters group related security topics, such as:
- Risk management
- Access control
- Incident response
- Asset management
- Vendor management
Grouping requirements into clear themes helps organizations logically structure their security activities.
Requirements
Each chapter contains clear requirements or objectives describing what organizations must achieve. For example, a requirement might state that an organization must identify, document, and secure all critical assets.
Controls
Some frameworks describe controls as the concrete actions that an organization should implement to satisfy each requirement. Controls could include technical safeguards (like encryption), organizational processes (incident response plans), or physical security measures (secure access areas).
Tasks
In Cyberday, requirements and controls are covered with Tasks. Cyberday automatically breaks down framework requirements into actionable, universal tasks. These tasks support multi-compliance: complete the task once and it's completed for all frameworks that have similar requirements.
Read more: How Tasks work
Practical examples: NIS2 and ISO 27001
Frameworks differ slightly in how they structure these elements. NIS2, for instance, follows this structure:
Directive Articles → Obligations (eg. Incident reporting) → Practical actions (eg. Establish an incident response and reporting process.)
ISO 27001 has a slightly different structure:
Clauses/Annex A → Control objectives (eg. Access Control) → Specific controls (eg. User access management
We’ve written more about ISO 27001 here, and also created a detailed comparison of ISO 27001 vs NIS2, highlighting key differences between these two frameworks.

Categories of frameworks
Cyber security frameworks can be grouped into different categories based on their scope, origin, and target audience. Understanding these categories helps organizations select the frameworks most relevant to their operations.
Global frameworks
Global frameworks are standards that recognized and used internationally. They provide a universal language and structure for security management and are often referenced by regulators, industry bodies, and customers.
- ISO 27001 – Information security management standard developed by the International Organization for Standardization.
- NIST CSF – Cybersecurity Framework by the US National Institute of Standards and Technology, widely adopted outside the US as well.
EU-wide frameworks
European Union sets cyber security directives that apply to all member states and organisations operating within them. These frameworks create a harmonized set of rules across the region.
- NIS2 – Directive on measures for a high common level of cybersecurity across the EU.
- GDPR – General Data Protection Regulation, setting strict rules for personal data protection.
- CRA – Cyber Resilience Act, focusing on cybersecurity requirements for products with digital elements.
- DORA – Digital Operational Resilience Act, setting ICT risk requirements for the financial sector.
Read more: Comparing EU Frameworks
Local (national) frameworks
Country-specific frameworks address national cybersecurity needs or legal requirements.
- Finnish Act on Information Security – National legislation for information security in critical sectors.
- German IT-SiG – IT Security Act, strengthening cybersecurity requirements for operators of critical infrastructures.
Certain bigger countries have frameworks and regulations that are also used as benchmarks in other countries as well.
United States
- HIPAA – Health Insurance Portability and Accountability Act, protecting health information.
- SOC 2 – Service Organization Control report for security, availability, processing integrity, confidentiality, and privacy.
- CMMC – Cybersecurity Maturity Model Certification, required for defense contractors.
United Kingdom
- Cyber Essentials – UK government-backed certification scheme focusing on basic cyber hygiene.
Industry-specific frameworks
Some frameworks target specific industries with unique security requirements.
- TISAX – Trusted Information Security Assessment Exchange, for the automotive industry.
- PCI DSS – Payment Card Industry Data Security Standard, for organizations handling card payments.
Modular approach to frameworks and how frameworks overlap
Many cyber security frameworks include similar requirements, even if they use different wording or structures. Common topics like access control, incident response, and asset management appear across most frameworks. This overlap creates opportunities to manage compliance more efficiently.

By taking a multi-framework approach, organizations can design a single set of security tasks that satisfy multiple frameworks at once. For example, enabling multi-factor authentication (MFA) might be a single control in your system, but it can simultaneously fulfill requirements in GDPR, ISO 27001, and NIS2. This avoids duplicated work and keeps compliance efforts consistent.
You can read more about the concept in our dedicated article: What is a modular cyber security framework?
Mini-case: managing ISO 27001, NIS2, and GDPR together
A mid-sized SaaS provider in the EU uses ISO 27001 to structure its security management system, while also needing to meet NIS2 and GDPR requirements. Instead of treating each framework separately, they built a unified task list in Cyberday:
- Task: Enable multi-factor authentication for all accounts
- Mapped to ISO 27001 Annex A.9.4.2 (secure log-on procedures)
- Mapped to NIS2 Article 21 (cybersecurity risk management measures)
- Mapped to GDPR Article 32 (security of processing)
- Task: Maintain an incident response plan
- Mapped to ISO 27001 Annex A.16 (information security incident management)
- Mapped to NIS2 Article 23 (reporting obligations)
- Mapped to GDPR Articles 33–34 (data breach notifications)
By implementing this approach, the company can mark a task as complete once, and the compliance status updates across all mapped frameworks automatically. This reduces audit preparation time and keeps their security program organized without redundant documentation.
How frameworks work in Cyberday?
Cyberday is built to help organizations manage multiple security frameworks in one place. The system transforms high-level regulations and standards into concrete tasks your team can track, assign, and complete.
1. Selecting your frameworks
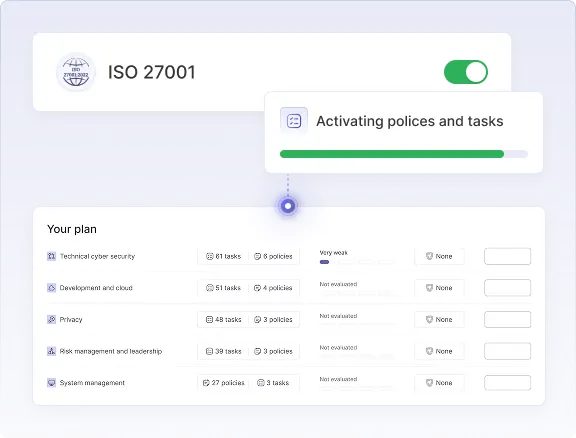
The process starts by choosing the frameworks that apply to your organization from Cyberday’s framework library. Cyberday has the widest support for global and local frameworks. This includes global standards like ISO 27001 and NIST CSF, EU-wide regulations like NIS2 and GDPR, national laws, and industry-specific frameworks such as PCI DSS or TISAX. The library is kept up to date, so any new requirements are added automatically.
2. Automatic breakdown into tasks
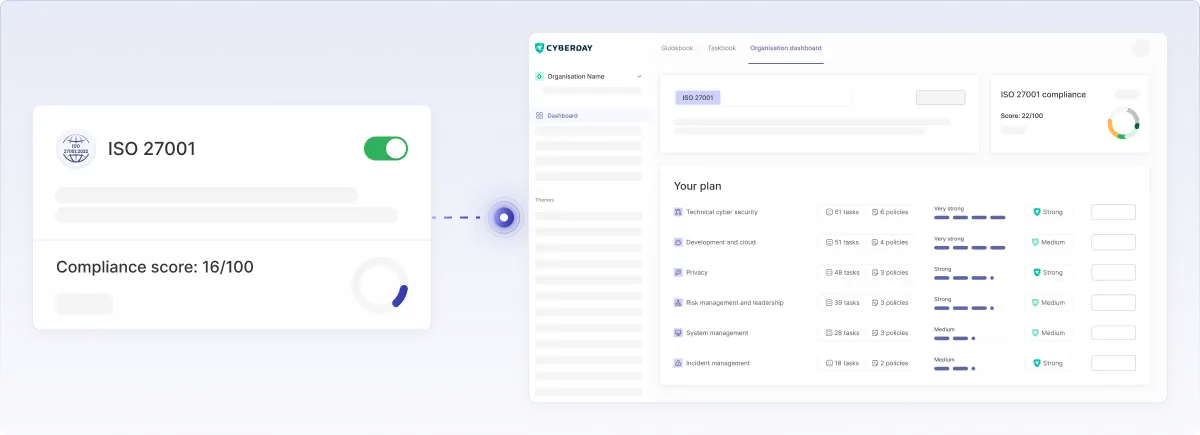
Once a framework is activated, Cyberday automatically breaks it down into clear, actionable tasks. Each task is linked to the exact control or requirement it fulfills, written in plain language to make implementation straightforward. This eliminates the need to manually interpret dense legal or technical text.
3. Multi-framework mapping
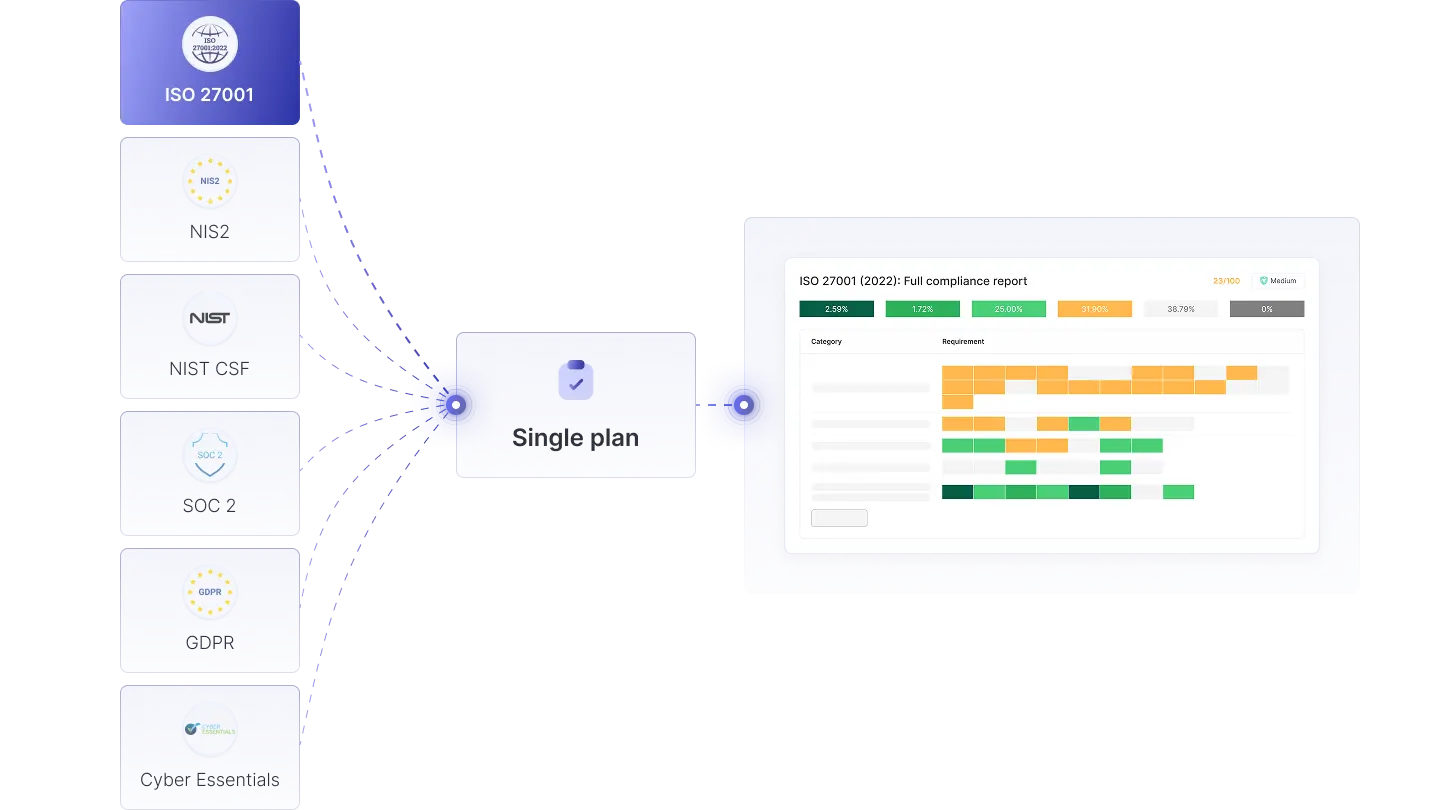
Many frameworks share the same requirements. Cyberday maps these overlaps so one task can satisfy multiple frameworks at the same time. For example, enabling multi-factor authentication may appear once in your task list but is linked to relevant clauses in ISO 27001, NIS2, and GDPR. This reduces duplicate work and ensures consistency.
4. Tracking and reporting
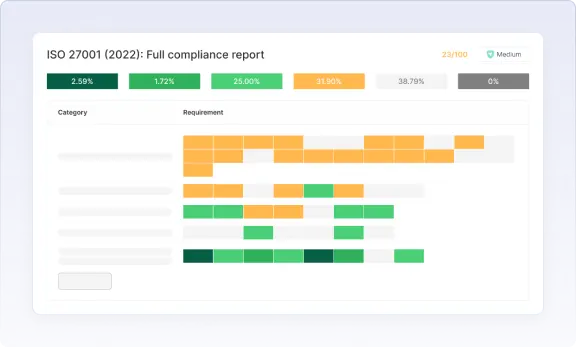
Completing a task updates your compliance status across all frameworks where it applies. Cyberday also provides framework-specific reporting views, allowing you to quickly show auditors and stakeholders your level of compliance, along with documented evidence for each control.
5. Staying compliant over time

Frameworks are not static. Cyberday monitors updates to laws and standards, automatically adjusting your tasks when requirements change. You’ll see new or updated tasks flagged in your workspace, making it easier to maintain compliance without starting from scratch.
To get started on your compliance journey, start your free Cyberday trial to see how it works in practice!
Frequently asked questions about frameworks
What is the difference between a framework and a standard?
A framework is a structured set of guidelines or requirements that outlines what organizations must achieve to improve security or meet compliance. A standard is a formally agreed specification, often created by recognized bodies like ISO, that defines exact criteria for implementation. In short, a framework is broader, while a standard is more prescriptive.
Which cyber security frameworks are legally required?
Examples include GDPR and NIS2 in the EU, HIPAA in the US healthcare sector, and APPI in Japan. These have legal consequences for non-compliance.
Can one framework cover multiple laws or regulations?
Partially. A single framework like ISO 27001 can help meet requirements from multiple laws, but you may still need additional measures to fully comply with each specific regulation.
What is a control in a cyber security framework?
A control is a specific safeguard, process, or technical measure implemented to meet a requirement in a framework. Examples include enabling MFA, encrypting data, or maintaining an incident response plan.
Do I need certification to be compliant with a framework?
Not always. Certification is often voluntary but provides external proof of compliance. Some contracts or industries may require it.
How often are frameworks updated?
Updates vary. Some, like ISO 27001, are revised every several years. Regulatory frameworks like GDPR are updated less often but may be clarified or supplemented with new guidance.
Which frameworks are best for small businesses?
ISO 27001 and NIST CSF are commonly used for structured security programs. For smaller UK companies, Cyber Essentials is a lightweight, accessible option.
What happens if a company fails to comply with a framework?
Consequences can include financial penalties, loss of certifications, reputational damage, and in some sectors, restrictions on doing business.

.svg)
























