NSM ICT Security Principles (NSM ICT SP) are Norway’s national recommendations for securing information and communications technology. Published by the Norwegian National Security Authority (NSM), they explain what an organization should do to protect information systems against unauthorized access, damage, and misuse.
The guidance is relevant across Norway for all public and private organizations, with a primary focus on operators of critical civic functions and critical infrastructure. It is advisory, not mandatory, and must be adapted to each organization while aligning with applicable laws such as the Norwegian Security Act.
At a high level, the principles group concrete measures into four categories that cover the full lifecycle of ICT: Identify, Protect and maintain, Detect, and Respond and recover.
They apply to both in-house and outsourced or cloud services, and the organization remains responsible for security when using providers, including reviewing the provider’s controls.
This article gives a plain-language NSM ICT Security Principles overview and guide, and it helps you understand the core NSM ICT Security Principles requirements so you can plan compliance work.
Read also: Norwegian NIS2 – Digitalsikkerhetsloven
What does NSM ICT Security Principles require?
NSM ICT Security Principles requirements are organized into four categories. Here is what you are expected to implement under each.
1) Identify
- Map deliverables, services, systems, devices, users and access needs.
- Define user categories, roles and responsibilities, including external providers.
- Use this understanding to prioritise security work and keep it current.
2) Protect and maintain
- Build security into procurement and development.
- Establish a secure ICT architecture with integrated functions like identity, device control, logging, IDS/IPS, backup and restore.
- Harden configurations, segment networks, and control identities and access.
- Protect data at rest and in transit with appropriate crypto and key management.
- Include security in change management and urgent changes.
3) Detect
- Run regular vulnerability assessments and handle known threats.
- Establish security monitoring and define what to collect and why.
- Analyse monitoring data, use automation where helpful, and surface anomalies.
- Perform penetration tests to verify defences and improve preparedness.
4) Respond and recover
- Prepare an incident management plan, roles, training, communication and third-party support.
- Perform business impact analysis and set restoration criteria.
- Assess, categorise, control and manage incidents, then evaluate and learn.
Taken together, the four categories form a simple loop: identify what you run, protect it, detect issues fast, then respond and recover to improve. Next, we show how these measures turn into practical security gains across architecture, operations, and incident handling.
How does NSM ICT Security Principles provide security?
The NSM ICT Security Principles drives a risk-based program across four areas. You first understand your organization and assets, then establish a secure state through architecture, hardening, identity and encryption. You add monitoring and vulnerability management to spot issues quickly, and you prepare incident response to recover and improve.
Together these measures create a strong defense against cyber threats and guide procurement and operations choices.
What are benefits of NSM ICT Security Principles?
Following the framework offers practical benefits:
- A clear, prioritized baseline for ICT security work that management can own.
- Practical measures that reduce exposure and help prevent, detect, and recover from incidents.
- Procurement and outsourcing guidance so security requirements are specified and verified with providers.
How long does it take to get NSM ICT Security Principles compliant?
Typical ranges, depending on size, scope, and current maturity:
- Starting from low maturity: 6 to 12 months
- With partial practices in place: 3 to 6 months
- With a mature ISMS like ISO 27001: 2 to 4 months to align specifics
Big variables include number of systems and suppliers, change management discipline, and availability of staff to run risk, architecture, hardening, monitoring, and incident response work.
Using tools like Cyberday can help streamline the process by providing guidance and resources.
Free tool: Assess your NSM ICT Security Principles compliance with our free assesment
FAQs
Is NSM ICT Security Principles mandatory?
No. They are recommendations. Separate legal frameworks can impose stricter or different requirements, such as Norway’s Security Act.
Why is NSM ICT Security Principles important?
It gives all organizations a structured set of measures to protect information systems and cut through conflicting advice. Following it builds a good baseline and helps leadership make informed security decisions.
Who needs to comply with NSM ICT Security Principles?
It is most relevant to organizations responsible for critical civic functions and critical infrastructure. NSM recommends it for all public and private organizations, including those that outsource ICT services.
When is NSM ICT Security Principles in effect?
The NSM ICT Security Principles have been in effect since 28 August 2017, when version 1.0 was first published in Norwegian. The current version is 2.1, with the English edition released on 31 May 2024
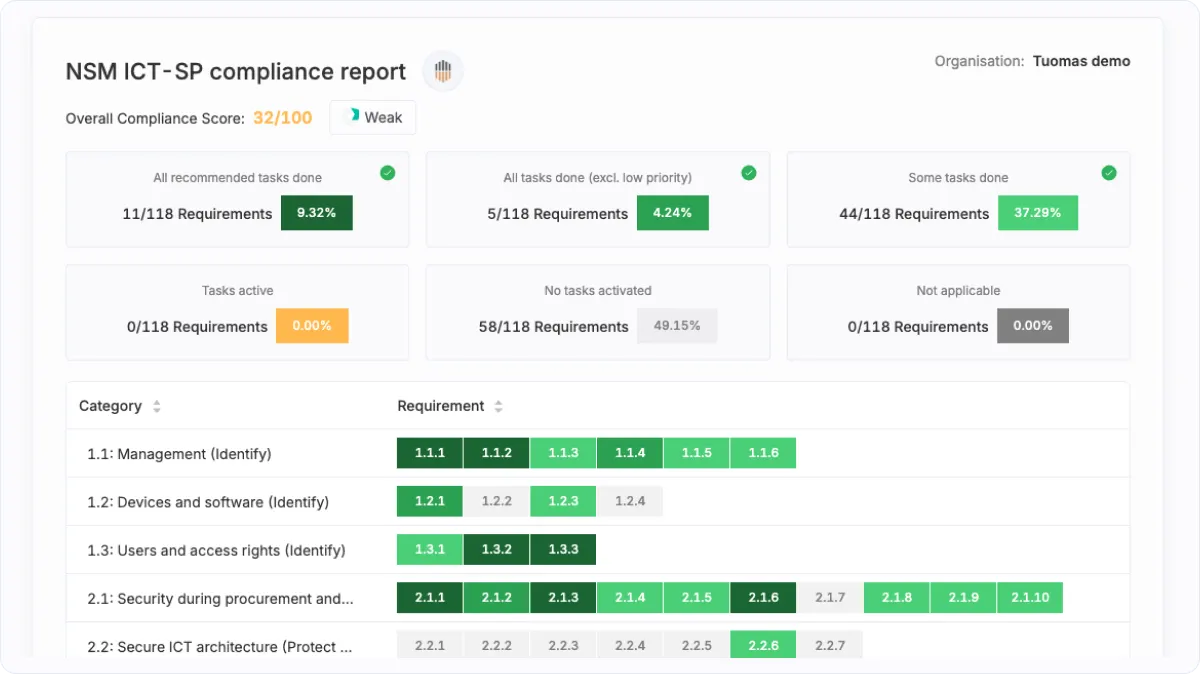
Is NSM ICT Security Principles supported in Cyberday?
Yes. Cyberday includes NSM ICT SP with ready-made tasks, documentation, and tracking.

.svg)
























