
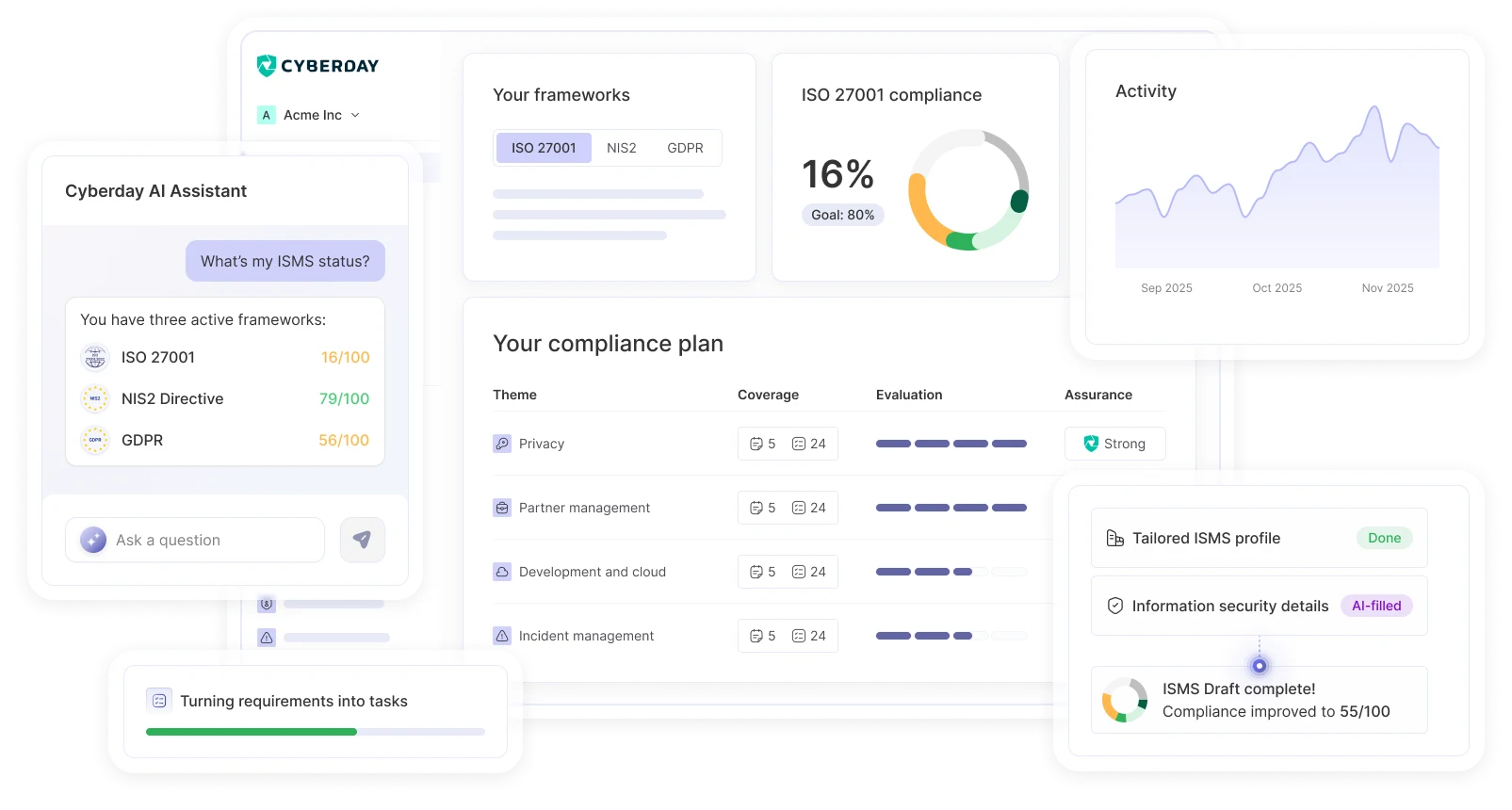
Achieve continuous, evergreen resilience with a long-term ISMS solution, not just a one-off project. Simplify and speed up your compliance work with Cyberday AI Agents.
Cyberday AI gives you the quickest, affordable and credible way to build your ISMS and get compliant with any relevant security framework for you. Start free in minutes.
.svg)
.png)
.png)
.png)
































The Critical Entities Resilience (CER) Directive is an EU law focused on strengthening the resilience of critical entities providing essential services across various sectors, ensuring they can withstand a range of threats and hazards.


The Belgian Law of 1 July 2011 on the security and protection of critical infrastructures establishes a security and protection framework for critical infrastructure. It mandates protective measures for critical infrastructure and implements EU directive 2008/114/EC.


The Cyber Resilience Act is an EU regulation for improving cyber security and cyber resilience in the EU. It includes requirements for hardware and software products with digital elements.


The European Union NIS2 has been transposed in Belgium into national law as the NIS2 law. The law closely aligns with the EU NIS2 directive and features only minor national differences. It obligates and defines cybersecurity rules for companies registered in Belgium working in the critical sector.


The DORA RTS on simplified ICT risk management describes the key elements that financial entities subject to lower scale, risk, size and complexity need to have in place to manage risks.


The Digital Operational Resilience Act (DORA) is the EU law on digital operational resilience. It aims to strengthen resilience in all aspects of financial institutions.


The CyberFundamentals framework is created by Centre for Cyber security Belgium. It provides a set of concrete measures to protect your data, significantly reduce the risk of the most common cyber-attacks, and increase your organisation's cyber resilience.


NIS2 sets the baseline for cybersecurity risk management measures and reporting obligations across important industries covered by the directive.


Full, certification-level ISMS. Complete set of security controls along with management, auditing and risk evaluation aspects.


GDPR sets out the requirements for lawful processing of personal data and demonstrating the adequate protection of data.
















.svg)

2NS is an independent Finnish cyber security enterprise. We operate as partners for our clients in the management of information security risks. We help our clients take care of their information security in a comprehensive manner, including both administrative and technical security. The elements of our operations are solid expertise and constantly evolving know-how, which are guided by satisfied clients.




















.png)
Above IT offers advanced technology solutions to boost business processes and productivity. Our services include cloud computing, cybersecurity and IT consulting, customised for different industries and organisations. We leverage cutting-edge technology to help IT departments reach their goals efficiently and securely. We are your trusted advisors and ’consigliere’ on this journey.



















Our best clients come to us because…
They realize that cybersecurity is no longer just an IT concern — it’s a strategic business risk. Triggered by European legislation like NIS 2 or DORA, they seek a more holistic approach to cybersecurity and risk management that goes beyond tool deployment or technical fixes.
They typically are…
CISOs, CIOs, or Compliance & Risk Officers in European mid-sized organizations (especially in Belgium), operating in sectors like healthcare, government, SaaS, critical infrastructure, or manufacturing — often overwhelmed by fragmented IT projects and increasing regulatory pressure.
They usually struggle with…
A patchwork of uncoordinated IT security tools, lack of executive-level policies on cyber resilience, and poor alignment with legal and regulatory frameworks. They often lack the in-house expertise to develop or manage a full cybersecurity management system.
They can expect from us…
A clear, structured cybersecurity program aligned with NIS 2, ISO27001, DORA, and cloud security best practices — including governance, implementation support, and policy development. As their part-time CISO (vCISO), we bring clarity, compliance, and concrete cyber resilience to their entire organization.
Here’s how we help…
We begin with a targeted assessment using proven frameworks like CyberFundamentals, identifying key weaknesses in risk management, resilience planning, and compliance posture. From there, we take an active role in designing and managing implementation programs. We connect the dots between IT security, business continuity, and compliance, and bring leadership clarity, governance structures, and operational alignment.







































DG Creative helps organizations and businesses choose, implement, and benefit from world-leading technology. Our goal is to create value for your operations through digital services and solutions. We are dedicated to cybersecurity, handling both the planning and implementation of physical networks, and consulting our customers to meet formal requirements set by legislation. With offices in Jakobstad and Vasa, we primarily serve Ostrobothnia but also have projects nationally and internationally. As an independent company and member-owner of Data Group, we provide resources across Finland. Our operations are ISO 9001 certified, ensuring high quality and continuous improvement.


















Dizparc Secured is an independent cybersecurity specialist’s company who works with offensive, defensive, and strategic cybersecurity. Our offering ranges from offensive services such as penetration testing, vulnerability assessments, red team operations to defensive services such as monitoring, investigations, forensic analyses, threat hunting, etc. We help organizations to analyse and mitigate risks and to establish a structured cybersecurity way-of-working.

















.png)
Dunamis Technology is a Norwegian specialist firm helping organizations govern and protect their values in an increasingly digital and highly regulated world. We make digital security understandable, practical, and value-driven— with a strong focus on leadership, governance, and regulatory compliance.
We deliver services within strategic digital security, GRC, and security leadership as a service. This includes vCISO, continuous operational protection through Dunamis Shield, and structured security governance via Dunamis Guardian. Our services are designed for organizations that need control, predictability, and documented compliance, without having to build large internal security teams.
Dunamis Technology has deep expertise in international ISO standards and frameworks, including ISO 27001, ISO9001 and ISO14001, as well as regulatory and legal requirements such as DORA, GDPR, NIS2, and national ICT regulations like NSM ICT Security Principles (NSM IKT Grunnprinsipper) and the Norwegian Act relating to national security (Security Act)(Lov om nasjonal sikkerhet (sikkerhetsloven).
We combine structured governance, hands-on execution, and modern tools to ensure that security works in practice and not just on paper. Our mission is to make organizations more resilient in a digital world. Our vision is “A digital world everyone can trust.”




















Enter SystemSolutions Oy is a Finnish IT consulting company that provides comprehensive IT solutions for businesses and organizations. We design, implement, maintain, and support complex technology solutions, focusing on the development of IT environments, cybersecurity, and ensuring business continuity.
Enter is a trusted reseller and implementation partner of the Cyberday service. With our deep expertise in the demands of critical industries, we help our clients stay compliant and secure. We also use Cyberday ourselves to ensure our own ISO 27001 compliance



















Integral Oy is a Finnish IT company that offers comprehensive digital solutions, combining people, information and technology to support its customers' business and growth. In terms of information security, we offer, among other things, information security plans, secure network solutions and ongoing consulting, ensuring the protection and reliability of business-critical information.





















KYBERX helps Baltic businesses build cyber-smart teams and automate compliance using proven platforms and practical support. By focusing on 𝐂𝐲𝐛𝐞𝐫 𝐀𝐰𝐚𝐫𝐞𝐧𝐞𝐬𝐬 and 𝐂𝐨𝐦𝐩𝐥𝐢𝐚𝐧𝐜𝐞 𝐀𝐮𝐭𝐨𝐦𝐚𝐭𝐢𝐨𝐧 we help growing businesses reduce risk, save time, and build real resilience without needing a big team or a big budget.




















Lawder Oy is a consulting company specialized in data protection and information security, helping organizations meet the practical and regulatory requirements of EU data governance. We act as external Data Protection Officers (DPOs) and use the Cyberday Digital Security Model to support our clients' daily governance work. Combining legal expertise with technology and security, we provide pragmatic, regulation-compliant solutions to support digital services and operational processes.


















Lenz is a multidisciplinary consulting firm that helps clients with growth and development projects. We specialize in identifying the most talented young professionals, combining potential with expert experience, and fostering inspiring leadership — a key factor in the success of many different types of projects.


















OdinCS delivers comprehensive cybersecurity solutions, integrating strategy, people, technology, and policy. Our tailored approach supports organizations at any cyber maturity stage:
With 40+ years of expertise, we provide customized solutions to stay ahead of threats. As a Nordic distributor and reseller, we connect top cybersecurity suppliers with dealers and key customers.



















Security is at the heart of what we do at Opensight. Our approach is based on three inextricably linked pillars: People, Process and Technology. We strive to improve your security quickly and cost-effectively, so that it fits seamlessly with your business needs.
Our focus 'People' focuses on strengthening your internal cyber security culture. We strongly believe in the power of your employees as the first line of defense against potential attacks. Through targeted training, awareness activities and ongoing guidance, we turn your teams into experts in recognizing and averting digital threats.
In the 'Process' category, we strengthen your defenses by implementing cyber security processes that integrate seamlessly into your business operations. Our tailor-made cyber security processes are designed for efficiency, enabling your organization to respond quickly to incidents, meet compliance requirements, and control risk. Effectively strengthen your business against cyber threats.
Rely on our advanced 'Technology' stack tailored to your specific needs. From advanced threat detection, to automated response mechanisms, our technology tools empower you to stay one step ahead in the ever-evolving landscape of cybercrime. Protect your digital assets with innovative cyber security technology and increase your resilience against the continuous evolution of cyber threats.



















At Qastan, we’re the digital architects who keep your organization compliant without the headache. We lighten your workload so cybersecurity becomes a natural part of your daily operations—not an after‑hours hobby. Together with Cyberday.ai, we turn complex compliance into clarity, simplicity, and just a touch of fun.




















Straightforward and reliable IT services for whatever the day throws at you. We help businesses with IT support, cybersecurity, cloud setups and hardware – giving you one less thing to worry about.


















UnBreach is a Finnish managed security service provider (MSSP) founded in 2021. Our mission is to help Nordic security-conscious companies prevent and stop data breaches. We do it by reselling, implementing, monitoring, and managing best-in-class cybersecurity SaaS tools.




















Unitas provides consultancy services and solutions in compliance, IT, and information security. Founded in 2019, Unitas currently employs nearly 20 professionals and is based in Lystrup, Denmark. We serve clients throughout primary the Northern countries. Our customers are typically found in highly regulated sectors such as utilities, finance, and medical industries, but we also work with retail chains and hosting providers.
We operate as a workshop, emphasizing a pragmatic and straightforward approach to ensure that problems are truly solved. As a part of this we have adapted Cyberday as a favorite tool for documenting our customers security measures and compliance. Explore our website for the full service catalog.




















Unitas provides consultancy services and solutions in compliance, IT, and information security. Founded in 2019, Unitas currently employs nearly 20 professionals and is based in Lystrup, Denmark. We serve clients throughout primary the Northern countries. Our customers are typically found in highly regulated sectors such as utilities, finance, and medical industries, but we also work with retail chains and hosting providers.
We operate as a workshop, emphasizing a pragmatic and straightforward approach to ensure that problems are truly solved. As a part of this we have adapted Cyberday as a favorite tool for documenting our customers security measures and compliance. Explore our website for the full service catalog.




















Weigert Consulting supports organizations with deep expertise in IT and information security, particularly in the areas of ISO 27001, risk management, and BSI. The focus is on technology- and process-driven solutions for critical infrastructures and regulated industries, with particular experience in aviation, energy, and IT services.

















Cybersecurity Services: At XLENT Cyber Security, we specialize in providing tailored cybersecurity services to protect your business from evolving threats and securing your digital values. Our services include Information Security Management Systems, Security Assessments, Incident Response and Crisis Management, and technical audits and verifications to ensure the highest level of security for your digital assets.
Standards, directives and Regulations: We support your organization in adhering to different standards, directives and regulations to ensure the organization meets internal and external requirements, such as:
XLENT Cyber Security are proud partners with Cyberday.ai and utilizes the tool for an effective and efficient implementation of standards, directives and regulations.



















Through top-tier expertise, smart sustainable solutions, and strong partnerships with our customers, we turn technology into real value.
With the introduction of NIS2, DORA, and the Norwegian Digital Security Act, organizations in Norway are facing a new era of stringent requirements for effective security governance. At blinQ, we provide expert advisory services in security and compliance, helping customers establish a comprehensive and tailored approach to safeguard your operations and ensure regulatory compliance.
Our mission is to help your business not only meet the new standards, but also strengthen its resilience against any evolving digital threats. By implementing modern security frameworks, you create a safer environment for both your organization and your employees.
Get in touch with us today for a no-obligation discussion on how we can assist you.


















