Confidentiality, integrity and availability, the CIA triad / triangle, offers a model for planning information security and e.g. categorizing assets due to their priority.
What is CIA classification?
When you enable CIA classification for assets in Cyberday, you can start systematically selecting values for assets CIA values and derive the asset priority from there, instead of letting asset owners freely choose it without any method.
CIA (in this case) stands for:
- Confidentiality: Ensuring that sensitive data is only accessible to authorized individuals or systems, protecting it from unauthorized access.
- Integrity: Maintaining the accuracy and trustworthiness of data by preventing unauthorized modifications, alterations, or tampering.
- Availability: Guaranteeing that data and systems are accessible and operational when needed, minimizing downtime or disruption.
How to enable CIA classification in Cyberday?
From the organisation dashboard go to settings scroll down to advanced features and activate “Asset CIA priority classification”.

After this, you can select if you want the asset priority to be automatically calculated from the CIA evaluation selection.
How CIA classification works in Cyberday?
The feature adds a CIA evaluation in the top section of each asset documentation card. After you select a value for each section the card’s priority value will be calculated if the automatic calculation is enabled. Otherwise, the evaluation will only be documented on the card.
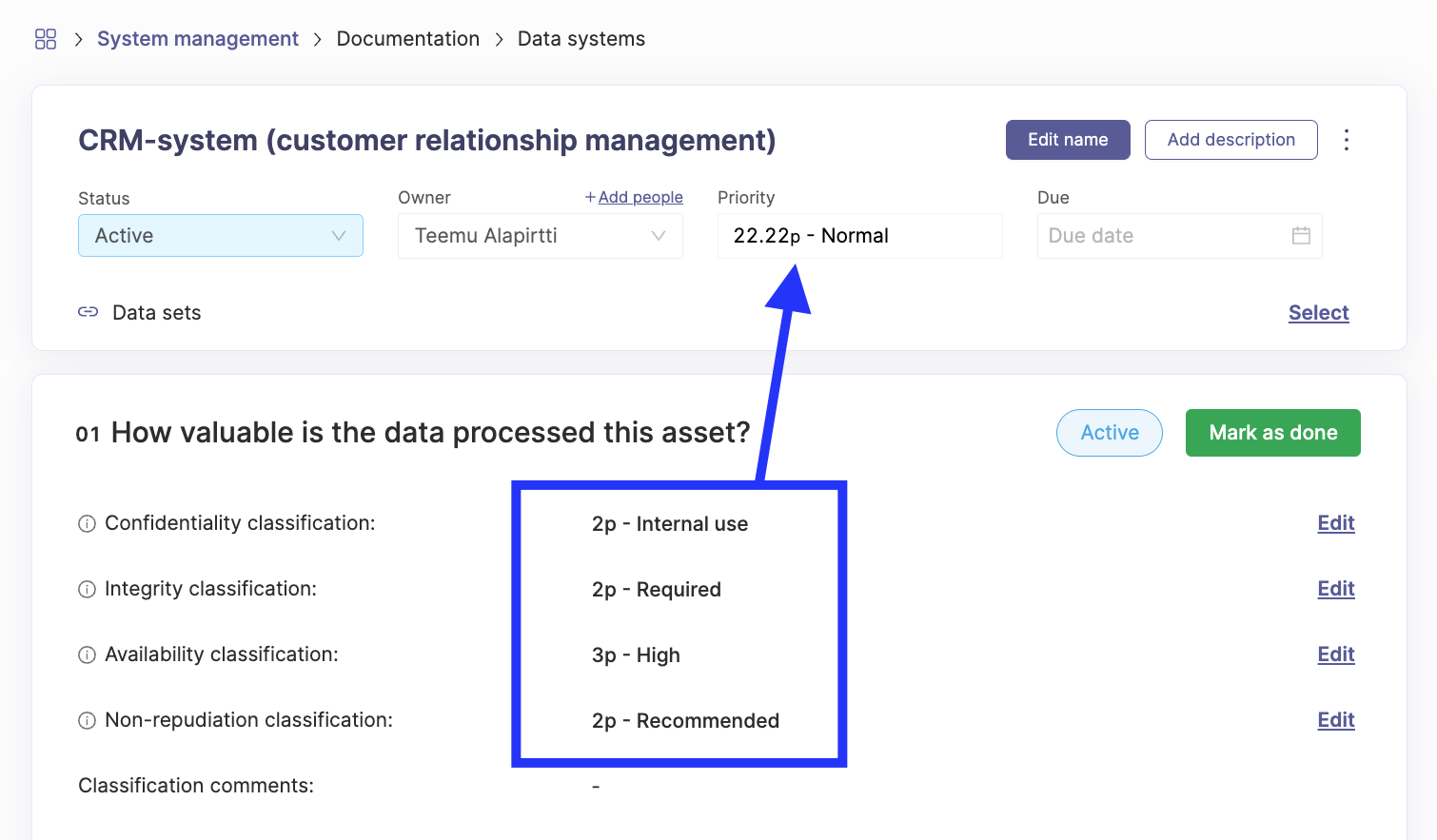
This view will be added to following documentation list items:
- Data systems
- Data sets
- Data stores
- System providers
- Other assets
- Offices
- Data processors
Benefits of using CIA classification
Using the CIA classification adds a bit of work for your asset management, but it can function as a great way for targeting your latter efforts more efficiently.
- Risk Assessment: It helps organizations assess and understand the potential risks associated with their assets. Organizations can identify vulnerabilities and threats that might impact their information and systems by evaluating confidentiality, integrity, and availability.
- Prioritization: It allows organizations to prioritize security measures and resources based on the importance of assets. Critical assets with high confidentiality, integrity, and availability requirements may require more robust security controls.
- Compliance: Many regulations and standards, such as GDPR, HIPAA, and ISO 27001, require organizations to protect the confidentiality, integrity, and availability of sensitive information. By evaluating assets with these principles, organizations can ensure compliance.
- Incident Response: Understanding the CIA's impact on assets helps organizations develop effective incident response plans. It guides the response to breaches or incidents that threaten these principles and helps mitigate potential damage.
- Resource Allocation: It helps organizations allocate resources effectively by focusing on assets most critical to the business. This ensures that security investments are made where they are needed most.
- User Awareness: Educating employees and users about the importance of the CIA principles can promote a culture of security within an organization, making them more aware of their role in safeguarding assets.
- Business Continuity: Protecting the availability of critical assets ensures that business operations can continue even in the face of disruptions, minimizing downtime and potential financial losses.










