Why invest on employee cyber security competence?
At their best, organisation's employees can be an active defense layer against cyber attacks. Active information security training and guidelines provide employees with up-to-date instructions and understanding, enabling them to prevent the occurrence of cyber security threats.
However, just awareness of phishing, malware, password attacks or other personnel driven security threats is not enough. Employees must adopt secure operating models that automatically reduce risks. It is also important for employees to know how to react when they detect something is off. Employees need to be trained on how to act in a secure way. It requires comprehensive training on information security and clear security guidelines.
Even a good set of guidelines may be disregarded if employees do not understand why such guidelines exist. Effective information security guidelines teach employees clear and secure practices. Ideally, the guidelines also explain why following the guideline is important.
When we help people in understanding related threats, provide clear guidelines, and explain why it is important to follow those guidelines, we give them the opportunity to act securely and protect our data and business. When employees are also asked to accept each guideline, a commitment to information security begins to form.
At its best, information security training and guidelines create a shared sense of responsibility. We are all contributing to the protection of our organisation's critical information. By engaging the entire staff with agile and intelligent practices, we promote the importance of security and the need for everyone's participation.
Competence of employees vs. technical security solutions
Many organisations may invest more directly in improving technical cyber security because such solutions can be implemented by a few key individuals without disrupting the rest of the organisation. Gartner predicted in 2018 that businesses would spend more than $124 billion on technical security solutions in 2019.
However, most cyber security breaches originate from human error that cannot be prevented by technical solutions alone. Without effective guidelines and training, employees can become easy targets for attackers. Often, the most effective way to enhance organisation's cyber security is to invest in these areas.
The organisation should guide employees to act securely when handling the organisation's information. Many of the guidelines also apply outside of the workplace. Preventing phishing, practicing secure mobile device usage, or adopting smart password practices can help employees improve the cyber security of their own families, for example.
The most significant personnel-driven security threats
We report real-life cases regarding cyber security weekly. Some threats are quite technical (such as unpatched vulnerabilities), but most of the threats that are prominent in modern times are personnel-driven. People are often the weakest link and the most effective target for cyber criminals to attack.
Some of the most important personnel-driven security threats in the present day include:
- Phishing, or fraudulent attempts to obtain sensitive information such as passwords by impersonating reputable entities, typically through means such as email, text messages, or phone calls.
- Malware, short for "malicious software," refers to unwanted programs such as viruses, bots, trojans, rootkits, and worms.
- Password attacks involve attackers exploiting the fact that employees reuse the same login credentials repeatedly.
- Ransomware, refers to malicious software that encrypts a victim's files and demands a ransom payment in exchange for access to the files. Today, attackers often threaten to release the compromised data or target the victim with further extortion.
- Business Email Compromise (BEC) is a form of cyberattack in which an employee's email is either compromised or impersonated to deceive colleagues or partners into making fraudulent bank transfers.
These are serious attacks that can originate from the carelessness of individual employees. That's why untrained employees are one of the organisation's biggest cyber security risks. Training and guidelines don't have to be complex and time-consuming; they can be agile and automated, but they must exist to mitigate risks.
Modern and automated approach
Our goal has been to create an awareness process in Cyberday that is closely integrated into the daily work routines of employees and is easy to maintain for all parties involved.
This is how the personnel's cyber security guidelines and training are implemented in Cyberday:
- Admins activate the desired cyber security guidelines in the app, either by using pre-existing examples or by adding their own guidelines.
- The guidelines can be targeted either to specific units or to the entire personnel.
- Cyberday Teams app and its dedicated bot ensure that employees notice and approve the guidelines directly within Teams.
- The guideline process can be expanded to include training content with just a few clicks.
PRE-MADE CONTENT FOR GUIDELINES THAT YOU CAN EXPAND YOURSELF
In Cyberday, you can find a list of suggested guidelines under different themes. These are general guidelines that are commonly repeated across various organisations.
The easiest way to implement a guideline is to activate it and target it to the entire personnel. However, you can also make changes to the guidelines and add completely unique ones.

Important themes in employee cybersecurity guidelines include:
- Safe password usage
- Identifying phishing attempts and safe email practices
- Proper handling of personal information
- Malware protection
- Recognizing and reporting security breaches
- Secure remote work and mobile device management
The guidelines are designed to be clear and concise, presented in small, manageable sections. This approach ensures that when employees click "Mark as accepted" they truly understand what is expected of them and are committed to following the instructions. Important info can get lost within long security guidelines.
TARGET THE APPROPRIATE GUIDELINES TO THE RIGHT EMPLOYEES
The guidelines should be relevant to employees so that they perceive them as necessary. Employees using mobile devices in the organisation should be instructed on updating them, those engaged in mobile work should be educated on data privacy while on the go, the IT department should be provided guidelines on securely setting up new software projects, customer service staff should be informed about registered data protection rights, and so on.

In the guidelines, there is no immediate need to aim for a targeted approach, but based on our experience, there are indeed aspects that can be addressed, provided that there is the opportunity for targeting and automated approval of the guidelines. In Cyberday, you can either target the guidelines to the entire staff or specific units that are managed by the admins designated as main users.
AUTOMATED MODEL FOR APPROVING GUIDELINES DIRECTLY IN TEAMS
Where do our employees spend a significant portion of their workday? In Microsoft Teams!
If we want our employees to notice the security guidelines and provide them with an easy way to read and adopt them, why not bring them to the place where employees already are?
In Cyberday Teams app, the bot takes care of reminding employees at appropriate intervals about unread or re-readable guidelines. By default, the bot sends reminders to employees once a month. The admins can define the time interval for re-reading the guidelines, for example once every 6 months or once every 12 months.
The reminder contains a clear request and a single link - go here to accept the guidelines. The employee's personal Guidebook view is just one click away from the message sent by the bot.
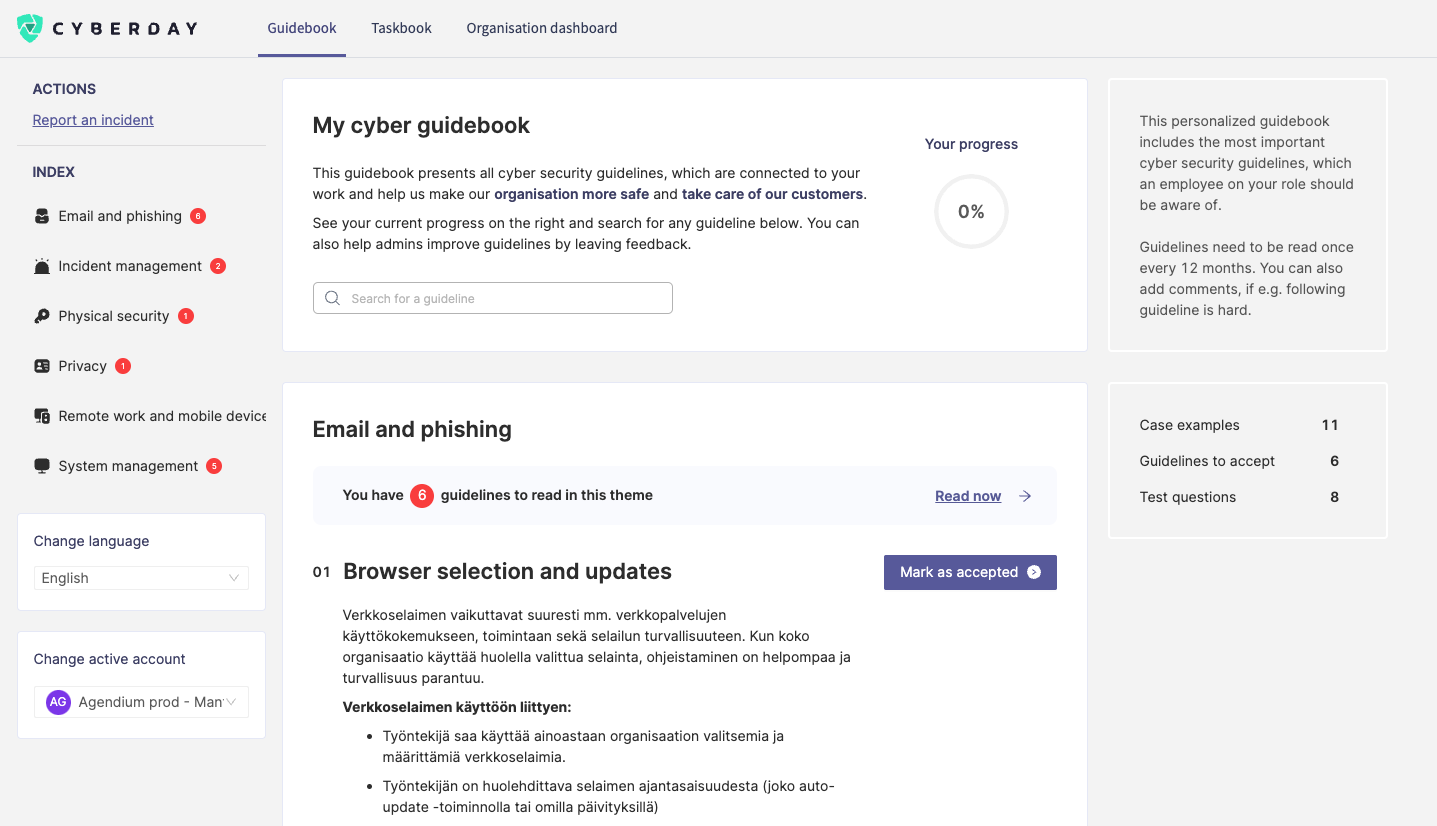
THE ADMIN IS ABLE TO SEE AN OVERVIEW OF THE OVERALL SITUATION
Some of the organisation's cyber security personnel should be responsible for the overall cyber security training and guidance.
To help these individuals, Cyberday's Organisation Dashboard provides summaries of different employees' responses to the guidelines. While the bot sends the reminders automatically, the summary helps the admins to react to the situation if needed.

EXPAND FROM GUIDELINES TO TRAINING
Straightforward guidance is often the fastest way to achieve cyber security, but when developing the competence of employees, long-term benefits are achieved by enhancing their cyber security understanding. In this way, they can best respond to new threats and situations safely.
When you want to invest more in developing the competence of your employees, you can utilize the Guidebook to expand the case examples and skill assessments of the guidelines.

The purpose of the case examples is to present real-life situations that have occurred due to non-compliance with the guidelines. By using these examples, the aim is to educate employees on why such guidelines exist, not just the guidelines themselves.

Yes, there could be instances when following security guidelines can be seen as boring or time-consuming. In these cases, understanding the risks associated with the guidelines can be the key motivator for employees to follow the guidelines in all situations.

The purpose of the skill tests is to assess the level of understanding and knowledge acquired after reading the guidelines. After reviewing the guidelines on a specific topic (e.g., remote work), employees are presented with multiple-choice questions that allow them to demonstrate their comprehension of the material.
Would you like to hear more about the topic?
If you would like to learn more about managing cyber security risks, join our upcoming webinars or pick a suitable time for a Teams meeting and we can continue the discussion in a more personalised manner.
.png)















.png)
